Welcome to yet another Cyber Threat Thursday blog where today we’ll be covering some types of attacks that are less commonly talked about, and how to defend ourselves from them.
Firstly, let’s start with a SYN attack.
Cyber threat- SYN Flood
Firstly, the word “SYN” is an abbreviation of “Synchronise” which is a TCP packet. An SYN flood attack is a type of Distributed Denial-Of-Service (DDoS) attack that is designed to overwhelm a server or network by flooding it with a large number of SYN requests.
These requests are typically sent by a botnet of compromised devices, making it difficult for legitimate requests to be processed.
To understand how an SYN flood attack works, it’s important to first understand how the Transmission Control Protocol (TCP) works.
TCP is a communication protocol that is used to establish a connection between two devices. When a device wants to establish a connection with another device, it sends a SYN (synchronize) packet to the destination device.
The destination device responds with an SYN-ACK (synchronize-acknowledge) packet, and the initiating device responds with an ACK (acknowledge) packet. This three-way handshake establishes a connection between the two devices.
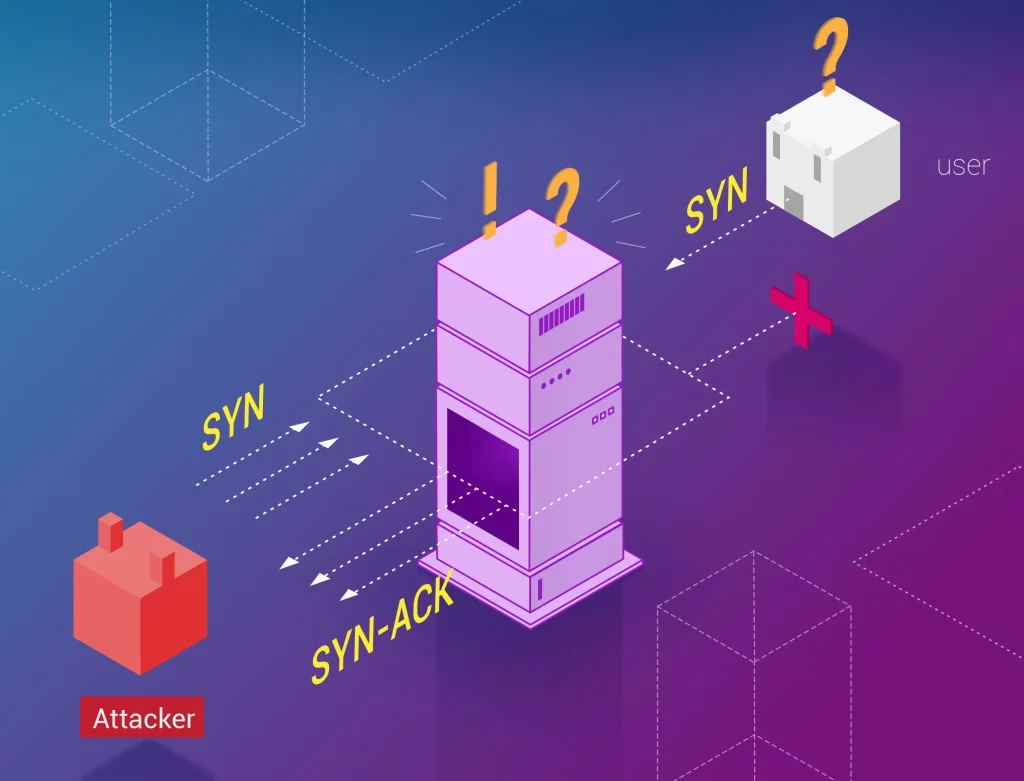
In an SYN flood attack, the threat actor sends a large number of SYN packets to the target device but does not respond to the SYN-ACK packets that the target device sends in response.
This leaves the target device waiting for the ACK packet that should follow the SYN-ACK packet, tying up resources on the device and preventing it from processing legitimate requests.
If enough SYN packets are sent, the target device can become overwhelmed and stop responding altogether.
Now we know what an SYN Flood attack is, let’s go over the best methods to defend yourself against this kind of Cyber threat.
Mitigation strategies
SYN flood attacks can be particularly difficult to defend against because they exploit a weakness in the way that TCP works. Because the target device is waiting for a response to the SYN-ACK packet, it has to allocate resources to maintain the connection, even if the connection is never completed.
This means that even if the attacker only sends a small number of SYN packets, they can tie up resources on the target device and prevent legitimate requests from being processed.
There are a few different techniques that can be used to defend against SYN flood attacks.
- One common technique is to use rate-limiting to limit the number of SYN packets that can be sent to a device in a given period of time. If manage your IT in-house or externally, this should ideally already be the case.
- Finally, network administrators can also use specialized hardware and software designed specifically to detect and defend against DDoS attacks, including SYN flood attacks. This could be achieved by using technologies like EDR, which we have made a blog about in itself here if you’re interested.
Cyber Threat- SQL Injection
Structured Query Language (SQL) is the most commonly used language for communicating with databases. However, it is susceptible to a type of cyberattack known as SQL injection.

The danger in this attack lies in the fact that in today’s digital world, databases play a crucial role in the storage and retrieval of data. Software like DbSchema and Microsoft Office Access rely on SQL for example, which is used in many workplaces to store large quantities of data.
SQL injection attacks occur when an attacker manipulates the data input of an SQL query in a way that the database executes unintended commands.
In other words, an SQL injection allows a threat actor to execute arbitrary SQL code in a database by exploiting vulnerabilities in the application’s software that interacts with the database.
Furthermore, a threat actor can retrieve sensitive data or modify, delete, or insert data into the database, potentially compromising the integrity and confidentiality of the system.
For instance, suppose a website contains a login form that requires a username and password. The website’s backend might use an SQL query to check the entered credentials against the database of users.
An SQL injection attack could manipulate the query in such a way that it always returns “true,” thus allowing the attacker to bypass the login form and gain unauthorized access to the system.
Now we’ve learnt what SQL Injection is, let’s go over the best methods to defend yourself against this kind of Cyber threat.
Mitigation strategies
There are several ways to protect against SQL injection attacks. One approach is to use prepared statements, which are pre-compiled SQL statements that can be parameterized.
This ensures that the user input is treated as data rather than part of the SQL query, thereby preventing the attacker from manipulating the query.
Another approach is to restrict user input by filtering out any characters that could be used for SQL injection. This involves checking user input for special characters, such as quotes or semicolons, and removing them before the data is processed.
Moreover, keeping your database software and web application frameworks up-to-date with the latest security patches can prevent SQL injection attacks from exploiting known vulnerabilities. This can be applied to all hardware and software updates on devices in general, we can’t stress the importance of it enough!
Cyber threat- Cross-Site Request Forgery (CSRF)
Cross-site request forgery attacks, also referred to as session riding or one-click attacks, is a malicious website exploit where a user on a trusted web application is forced to execute unwanted commands.
. In this attack, threat actors will craft a request that appears to be legitimate and send it to the target web application. The request is designed to perform an action on behalf of the user without their knowledge or consent.
If done correctly, the web application will accept the threat actors’ request, which could lead to them gaining access to sensitive information and more.
A good example of this in a real-life scenario would be this:
- A user logs into their bank account in one tab of their web browser and they visit a malicious website in another tab.
- The malicious website contains a form that automatically submits a request to transfer funds from the user’s account to the threat actor’s account.
- When the user is tricked into submitting the form, the browser sends the request to the bank’s website with the user’s authentication credentials. Because the request appears to be legitimate, the bank processes the transfer and the threat actor receives the funds.
Now we’ve learnt what a CSRF attack is, let’s go over the best methods to defend yourself against this kind of Cyber threat.
Mitigation strategies
Cyber Security Awareness training is a great way to learn methods to spot illegitimate websites and emails and should be provided to all employees in a business.
Not only is it cheaper to provide training than to suffer the consequence of a breach, but it’s also one of the most effective ways at avoiding potential attacks in the first place.
On the other hand, enabling Multi-factor authentication adds an additional layer of security by requiring users to provide a second form of authentication, such as a code sent to their phone or email, before certain actions.
Furthermore, this is generally a good Cyber Security practice to follow for other types of attacks too, such as cracking for example. This is because if the user cracked your password, they’d still have to get through another layer of security.
Conclusion
We hope you’ve liked this slightly longer blog format and that you’ll stick around to see our future releases, covering everything from recent IT News to Knowledgebase articles. Thanks for reading!